Tools like PuTTY are handy for ensuring our connections to important places, like databases, are safe. This blog post will talk about what is Putty configuration? how we connect to databases, why PuTTY is useful for that, and how it’s different from VPNs.
Features of PuTTY
SSH Connectivity: PuTTY is renowned for its robust support for SSH, which encrypts data transmitted between client and server, ensuring confidentiality and integrity.
Terminal Emulation: With its terminal emulation capabilities, PuTTY provides users with a command-line interface to interact with remote systems, execute commands, and manage files.
Session Management: PuTTY allows users to save connection configurations as sessions, making it easy to connect to frequently accessed servers with predefined settings.
Key Authentication: PuTTY supports public-key authentication, enabling users to securely authenticate themselves to remote servers without the need to enter passwords.
X11 Forwarding: Users can enable X11 forwarding in PuTTY to securely run graphical applications on remote servers and display them locally.
Port Forwarding: PuTTY offers port forwarding functionality, allowing users to securely tunnel specific ports between local and remote systems.
Why PuTTY?
Security: PuTTY prioritizes security, employing strong encryption algorithms to protect data transmitted over insecure networks.
Versatility: PuTTY supports multiple network protocols, making it suitable for various use cases, from remote server administration to file transfer.
User-Friendly Interface: Despite its powerful capabilities, PuTTY features a straightforward and intuitive interface, making it accessible to users of all skill levels.
Open Source: Being open-source software, PuTTY is freely available for download and can be customized or extended to suit specific requirements.
How to Access PuTTYgen
PuTTYgen is a dedicated key generation tool for the SSH (Secure Shell) protocol. It facilitates the creation and management of public-key cryptography for secure remote server authentication. In simpler terms, PuTTYgen acts as a cryptographic key management utility specifically designed for SSH connections. Here is the interface.
Getting Started with PuTTY
Download and Installation: PuTTY can be downloaded from its official website or installed via package managers on Linux distributions.
Configuration: After installing PuTTY, users can configure settings such as session parameters, terminal preferences, and key authentication options.
Connecting to a Server: To establish a connection, users simply need to enter the hostname or IP address of the remote server, along with their credentials if required.
Saving Sessions: Once a connection is established, users can save the session settings for future use, eliminating the need to re-enter configuration details each time.
What is Putty Configuration?
Session Configuration:
- Launch PuTTY.
- In “Host Name (or IP address),” enter the server’s hostname or IP address.
- (Optional) Assign a descriptive name to the session under “Saved Sessions.”
SSH Tunnel Configuration:
- Navigate to the “Connection” category on the left.
- Expand the “SSH” subcategory and then click on “Tunnels.”
- In “Source port,” enter any unused local port number (e.g., 3307).
- In “Destination,” enter the format: localhost:port_on_server (e.g., localhost:3306 for standard MySQL port).
- Click “Add” to create the tunnel.
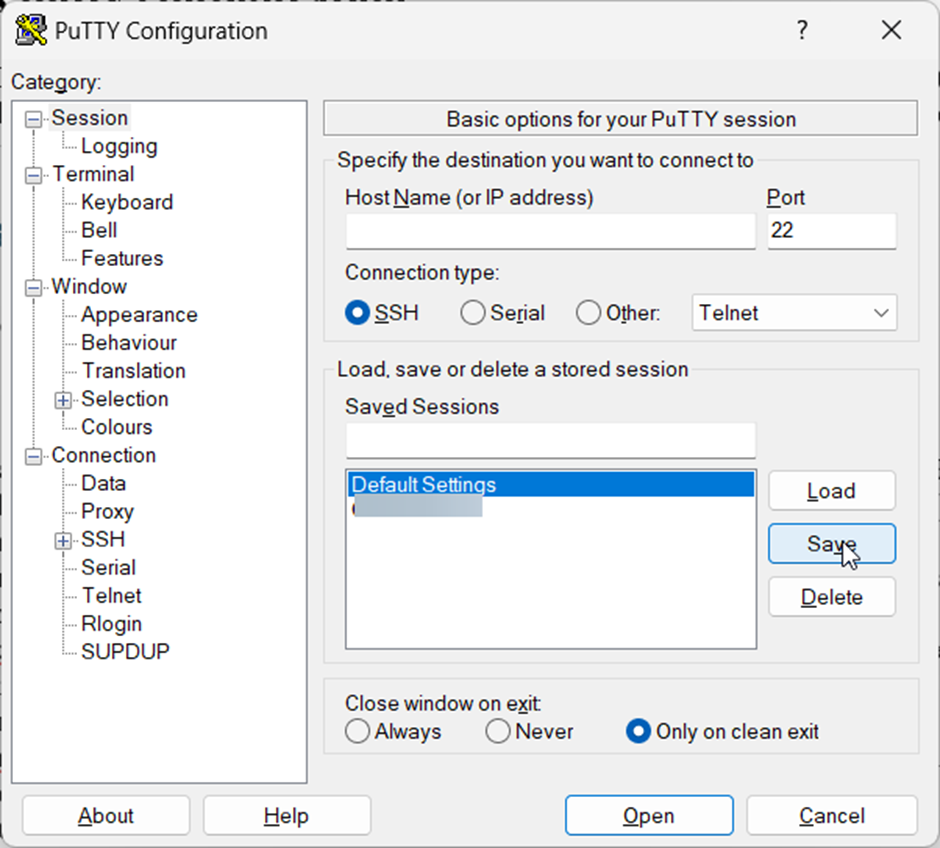
Saving the Configuration (Optional)
- Click “Save” under the “Session” category.
- Give your configuration a name for future use.
Connecting with your Database Tool
- Launch your database management tool (e.g., MySQL Workbench, pgAdmin).
- Host: localhost (since you created a local tunnel)
- Port: The port number you specified in the “Source port” field (e.g., 3307)
- Username and Password: Your database credentials
Your Secure Shell to the Database
PuTTY isn’t solely designed for databases, but it excels at establishing secure connections to remote servers, including database servers. Here’s a breakdown of its functionality:
- SSH Protocol: PuTTY leverages the Secure Shell (SSH) protocol, which encrypts communication between your machine and the server. This safeguards your login credentials and any data transfer, ensuring confidentiality.
- Command-Line Interface: Unlike a graphical user interface (GUI) for database management, PuTTY provides a command-line interface (CLI). You’ll interact with the server using text commands specific to the database software (e.g., MySQL, PostgreSQL).
Benefits of Utilizing PuTTY
- Enhanced Security: Encrypted communication shields your login details and data during transfer.
- Lightweight Footprint: PuTTY is a compact program, requiring minimal system resources.
- Flexibility: It functions across various operating systems and supports multiple protocols beyond SSH.
PuTTY vs. VPN
While both PuTTY and VPNs establish secure connections, their functionalities diverge:
- PuTTY: Creates a secure tunnel specifically for accessing functionalities on a remote server, often for database interaction or server administration.
- VPN: Creates a secure tunnel that encrypts all your internet traffic, allowing you to connect to a private network remotely. This is ideal for secure remote work or accessing geo-restricted content.
Here is the summary table of the
| # | Feature | PuTTY | VPN |
| 1 | Purpose | Secure connection to a remote server | Secure connection to a private network |
| 2 | Data Flow | Specific service (e.g., database) | All internet traffic |
| 3 | Encryption | Encrypts communication with the server | Encrypts all internet traffic |
| 4 | Use Case | Database interaction, server admin | Remote work, secure public Wi-Fi, accessing geo-restricted content |
Resources for Getting Started:
- PuTTY Download: [PuTTY official website]
- MySQL Tutorial: https://dev.mysql.com/doc/refman/8.0/en/tutorial.html
- PostgreSQL Tutorial: https://www.postgresqltutorial.com/
By understanding PuTTY and database connections, you gain the ability to interact directly with the data source, leading to more comprehensive and effective testing strategies. This empowers you to contribute significantly to the overall software quality assurance process.
Summary
For secure connections to databases, PuTTY is often the preferred choice. This blog addresses queries such as “What does PuTTY Configuration entail?” and provides a step-by-step explanation.
Additionally, it offers a clear comparison between PuTTY and VPN, given their related functionalities.